Try our Virtual Agent - It can help you quickly identify and fix common SMB issues.
Server Message Block (SMB) is a network transport protocol for file systems operations to enable a client to access resources on a server. The primary purpose of the SMB protocol is to enable remote file system access between two systems over TCP/IP.
SMB troubleshooting can be extremely complex. This article isn't an exhaustive troubleshooting guide Instead, it's a short primer to understand the basics of how to effectively troubleshoot SMB.
One key aspect of quality SMB troubleshooting is communicating the correct terminology. Therefore, this article introduces basic SMB terminology to ensure accuracy of data collection and analysis.
The SMB Server (SRV) refers to the system that is hosting the file system, also known as the file server. The SMB Client (CLI) refers to the system that is trying to access the file system, regardless of the OS version or edition.
For example, if you use Windows Server 2016 to reach an SMB share that is hosted on Windows 10, Windows Server 2016 is the SMB Client and Windows 10 the SMB Server.
Before you troubleshoot SMB issues, we recommend that you first collect a network trace on both the client and server sides. The following guidelines apply:
# tcpdump -s0 -n -i any -w /tmp/$(hostname)-smbtrace.pcap To discover the source of the issue, you can check the two-sided traces: CLI, SRV, or somewhere in between.
This section provides the steps for using netshell to collect network trace.
The Microsoft Message Analyzer tool has been retired and we recommend Wireshark to analyze ETL files. For those who have downloaded the tool previously and are looking for more information, see Installing and upgrading Message Analyzer.
A Netsh trace creates an ETL file. ETL files can be opened in Message Analyzer (MA), Network Monitor 3.4 (set the parser to Network Monitor Parsers > Windows), and Wireshark.
netsh trace start capture=yes report=yes scenario=NetConnection level=5 maxsize=1024 tracefile=c:\Temp\netTrace.etl New-NetEventSession -Name trace -LocalFilePath "C:\Temp\netTrace.etl" -MaxFileSize 1024 Add-NetEventPacketCaptureProvider -SessionName trace -TruncationLength 1500 Start-NetEventSession trace netsh trace stop Stop-NetEventSession trace Remove-NetEventSession trace You should trace only a minimum amount of the data that's transferred. For performance issues, always take both a good and bad trace, if the situation allows it.
SMB is an application-level protocol that uses TCP/IP as the network transport protocol. Therefore, an SMB issue can also be caused by TCP/IP issues.
Check whether TCP/IP experiences any of these issues:
If there is no noticeable TCP/IP issue, look for SMB errors. To do this, follow these steps:
Look at the actual SMB protocol details in the network trace to understand the exact commands and options that are used.
Compare the commands and operations to the protocol specification to make sure that everything is operating correctly. If it is not, collect data that is closer to or at a lower level to look for more information about the root cause. To do this, follow these steps:
Optionally, you might also temporarily uninstall the antivirus program during troubleshooting.
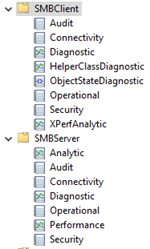
Both SMB Client and SMB Server have a detailed event log structure, as shown in the following screenshot. Collect the event logs to help find the root cause of the issue.

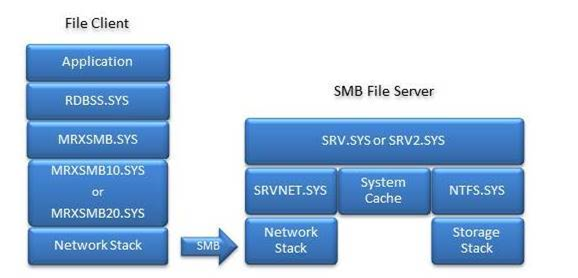
This section lists the SMB-related system files. To keep the system files updated, make sure that the latest update rollup is installed.
SMB Client binaries that are listed under %windir%\system32\Drivers:
SMB Server binaries that are listed under %windir%\system32\Drivers:
We recommend that you update the following components before you troubleshoot SMB issues: